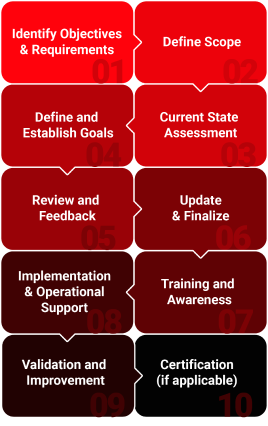
ISO 27001 Components
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a framework for organizations to protect their sensitive information and ensure compliance with relevant laws and regulations. Here are the key components of ISO 27001 compliance
A formal document outlining the organization's commitment to information security and its objectives.
Identifying and assessing potential threats and vulnerabilities to the organization's information assets.
Implementing a range of technical, organizational, and administrative controls to mitigate identified risks.
Establishing a systematic approach to managing information security, including processes, procedures, and documentation.
Regularly monitoring the effectiveness of security controls and conducting periodic reviews to identify areas for improvement.
Implementing procedures for handling and responding to security incidents.
Ensuring compliance with relevant data protection laws and regulations, such as GDPR and CCPA.
Assessing and managing risks associated with third-party service providers.
Providing security awareness training to employees to foster a security-conscious culture.
Conducting regular audits to assess compliance with ISO 27001 and seeking certification from an accredited certification body.