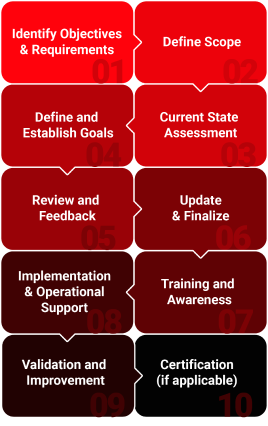
Mobile Application Penetration Testing Components
Mobile applications have become an integral part of our daily lives. However, their increasing complexity and reliance on sensitive data make them prime targets for cyberattacks. Mobile Application Penetration Testing is a crucial security measure that helps organizations identify and address vulnerabilities, ensuring the security and privacy of their users. Mobile application penetration testing involves several key components
Gathering information about the target mobile application, including its functionalities, platforms, and potential attack vectors.
Analyzing the application's source code to identify vulnerabilities like insecure coding practices, hardcoded secrets, and outdated libraries.
Testing the application while it's running to identify vulnerabilities like insecure data storage, weak authentication mechanisms, and insecure network communication.
Disassembling the application to understand its internal workings and identify potential vulnerabilities.
Automatically generating and injecting invalid inputs to identify unexpected behavior and potential vulnerabilities.
Attempting to exploit identified vulnerabilities to gain unauthorized access or compromise the application's security.
Documenting the findings of the testing process, including identified vulnerabilities, their severity, and recommended remediation steps.