Network Penetration Testing Components
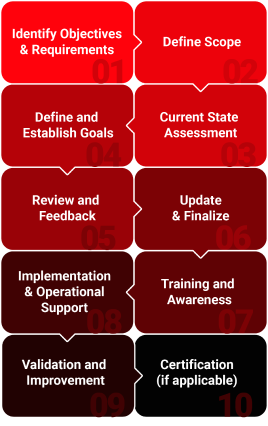
Network Penetration Testing is a proactive security measure that helps organizations identify and address vulnerabilities in their network infrastructure. By simulating real-world attacks, organizations can strengthen their security posture and protect their sensitive data. Network Penetration Testing involves several key components
Gathering information about the target network, including its topology, IP addresses, and open ports.
Using automated tools to identify potential vulnerabilities, such as outdated software, weak configurations, and open services.
Attempting to exploit identified vulnerabilities to gain unauthorized access to the network or its systems.
Once access is gained, attackers may escalate privileges, steal sensitive data, or deploy malware.
Documenting the findings of the testing process, including identified vulnerabilities, their severity, and recommended remediation steps.