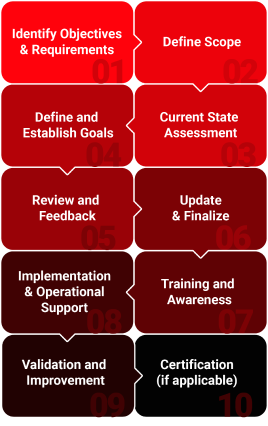
ISMS Components
An Information Security Management System (ISMS) is a framework of policies, procedures, processes, and technologies designed to protect an organization's sensitive information. Here are the key components of an ISMS
Set the foundation and derive implementation for information security controls and practices.
Identify, assess, and mitigate potential information and cyber security threats to the information assets.
Educate and empower your staff and foster a culture of security across the organization.
Identify, design and deploy organizational controls, personnel controls, technical controls, physical controls, and supplier security controls
Prepare in advance for responding to and recovering from security breaches in a timely and effective manner.
Measure the performance and assess the effectiveness of security controls to identify areas for improvement.
Assess the effectiveness of the ISMS to meet its objectives and compliance with regulatory, contractual, and business requirements.
Identifying and implementing changes to the ISMS to address evolving threats, vulnerabilities, and regulatory requirements.