Web Application Penetration Testing Components
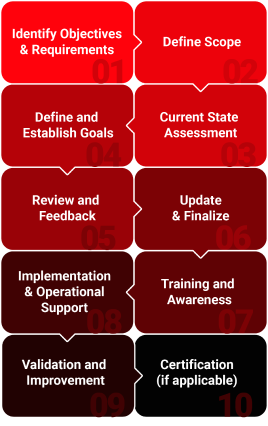
Web Application Penetration Testing involves several key components. By understanding these components, organizations can better assess the risks associated with their web applications and take appropriate measures to mitigate them.
This phase involves gathering information about the target web application, including its technology stack, network infrastructure, and potential vulnerabilities.
Automated tools are used to identify potential vulnerabilities, such as open ports, outdated software, and misconfigurations.
Attackers attempt to exploit the identified vulnerabilities to gain unauthorized access to the web application or its underlying systems.
Once access is gained, attackers may escalate privileges, steal sensitive data, or deploy malware.
A detailed report is generated, outlining the identified vulnerabilities, their potential impact, and recommended remediation steps.