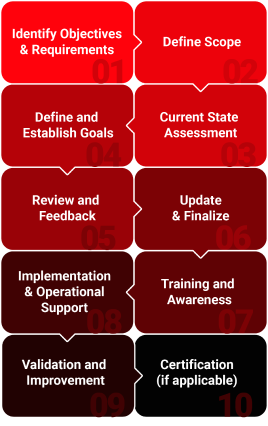
NIST SP 800-53 Components
The National Institute of Standards and Technology (NIST) Special Publication 800-53 is a comprehensive set of security controls that organizations can use to protect their information systems. It is a key component of the NIST Cybersecurity Framework.
Controls related to protecting sensitive data, such as encryption, data loss prevention, and access controls.
Controls related to securing applications, such as input validation, output encoding, and security testing.
Controls related to securing operating systems and other system components, such as patching, configuration management, and malware protection.
Controls related to securing networks, such as firewalls, intrusion detection systems, and VPNs.
Controls related to managing the security of third-party suppliers and vendors.
Ensures that individuals with access to sensitive information are trustworthy and qualified. It includes background checks, role-based access control, ongoing security training, and access revocation when personnel leave or change roles.
Protects an organization’s assets and facilities from unauthorized access and environmental threats. It involves access control measures (e.g., badges and security guards), secure areas for sensitive information, environmental monitoring, and visitor management.
Controls related to responding to and recovering from security incidents, such as incident response planning, forensics, and continuity planning.